CSCBE 2019: NOT_MALWARE
- 2 minutes read - 337 wordsBackground
I’m currently working as an intern at NVISO, doing work on Android Malware analysis.
When I was asked if I wanted to create a challenge, I immediately got to work!
After spending a couple of hours thinking about what kind of challenge I would create, and decided upon an Android challenge.
The good stuff
Building a good challenge is actually not that easy, you need to find a good difficulty level and make sure that the solution can be found in a reasonable amount of time.
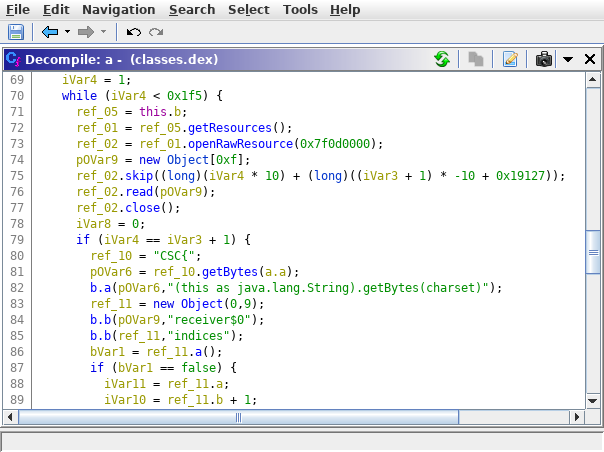
The flow to solve the challenge involves decompiling the APK, then noticing there is something funny about the pictures that it generates.
Once you got to the pictures, it should have been easy to see that there is Base64 encoded data appended to them.
Upon extracting and decoding the data, you’ve got your flag!
When I got the mail that they reviewed my challenge and accepted it, I was thrilled!
Internals
Everytime you run the app, it generates a new set of images. To do this, a random number is generated that decides where in the JPG it starts to read data that it will append.
To avoid participants from getting the flag by simply running grep, I decided to build the flag from data that was in the source JPG.
I ran strings against it and picked a random entry that it returned, then noted the offset at which it was placed.
This meant I had to hardcode the offset (0x19127), but a quick glance at that address would not have been likely to give away the flag, as it was a random occurrence in the file.
Solution
Here’s a simple script that solves the challenge for you:
#!/usr/bin/env bash
adb pull /sdcard/csc
for i in csc/*.jpg; do
tail -n1 $i | base64 -d | grep CSC{.*}
done
When you run it, it should spit out the flag:
CSC{v7bxt[_*ES}
I hope you enjoyed the challenge, I know I’m looking forward to seeing you all at the next edition already!